







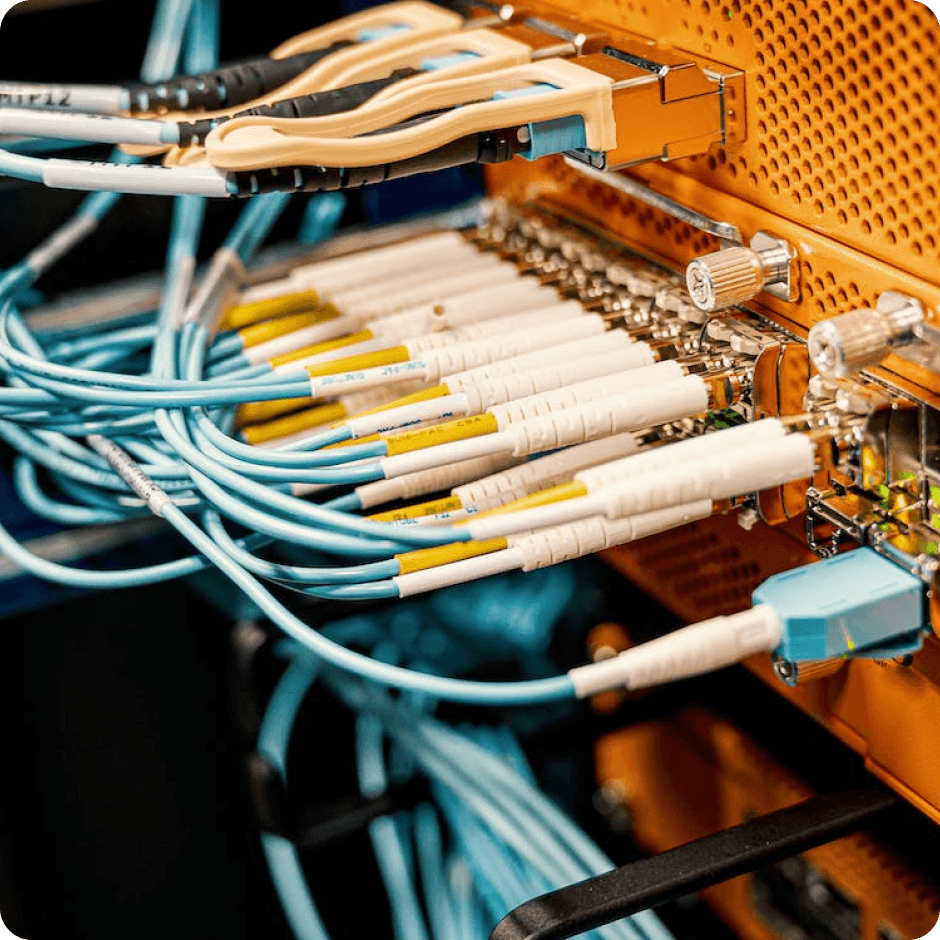
Configuration and management of network devices are done manually, leading to a time-consuming and error-prone process.
Define business requirements, we
will create outcomes with technology
We will bridge the gap with
necessary IT resources

We will support you in growing your in-house expertise
 Denmark
Denmark
kursus@insoftservices.dk
+45 32 70 99 90
 Germany
Germany
info@insoftservices.de
+49 6151 277 6496
 Netherlands
Netherlands
info@insoftservices.nl
+31 71 799 6230

 Norway
Norway
kurs@insoftservices.no
+47 23 96 21 03
 Sweden
Sweden
utbildning@insoftservices.se
+46 8 502 431 88
 Great Britain
Great Britain
info@insoftservices.uk
+44 20 7131 0263