Getting Started With Network Automation Architecture
- One of the main motivations towards adopting Network Programmability and Automation is building agile businesses. This is both in terms of deploying changes and dynamically troubleshooting network issues. Whilst doing things faster is nice, it isn’t always a problem that many enterprise organizations need to solve. Here are a few more motivations:
- Need for simplified architectures: Traditionally, most enterprise network devices are configured and maintained with numerous one-off network changes. These are hard to track and result in harder to manage “complicated” networks. With Network Programmability and Automation being factored in from the outset of architecture discussions, we can have simpler, repeatable, easier to maintain and automate networks. Here are some of the questions that need to be answered early on in the design process:
- Which features work across vendors?
- Which extensions work across platforms?
- What type of API or automation tooling works with particular network platforms?
- Is there solid API documentation?
- What libraries exist for a given product?
- Deterministic Outcomes: Making use of tried and tested network programmability and automation processes can help achieve predictability in the network. This does away with random ad hoc CLI changes.
- Need for simplified architectures: Traditionally, most enterprise network devices are configured and maintained with numerous one-off network changes. These are hard to track and result in harder to manage “complicated” networks. With Network Programmability and Automation being factored in from the outset of architecture discussions, we can have simpler, repeatable, easier to maintain and automate networks. Here are some of the questions that need to be answered early on in the design process:
Drawing a Network Automation Diagram

- Drawing a network automation diagram is the first step in the network automation architecture.
- A network automation diagram is a physical display of how the architecture will look like.
- One can see how things will connect and co-exist.
- A diagram can also help pinpoint issues in the architecture if the expected results are not achieved.
Steps of Making A Network Architecture Diagram
- Listing all the components that are to be present in the architecture is essential. Examples of network automation components include; the cloud, servers, clients, mainframes, peripherals, hubs, and routers (Majumdar et al., 2022).
- The next step is drawing lines between the components to see how they will connect. The lines should not crisscross each other to avoid confusion during development.
- The next step is to use a network diagram software to map out the diagram once the general layout has been established (Majumdar et al., 2022). The software tool should have readily available images to represent the components of the architecture. It should also provide a grid background to align items in the diagram easily and fit with the arrangement of the office.
- Customizing the diagram is the next step. Naming all the components available in the architecture is essential. Changing font, size, and color while naming is essential to outline the differences and levels of each element (Majumdar et al., 2022).
- Sharing the diagram with colleagues is the next step. This enables them to provide insights into the network architecture and conduct necessary editing on some areas for improvement.
- The physical implementation of the diagram is the final step.
Diagramatic Representation of Network Automation Architecture Diagram
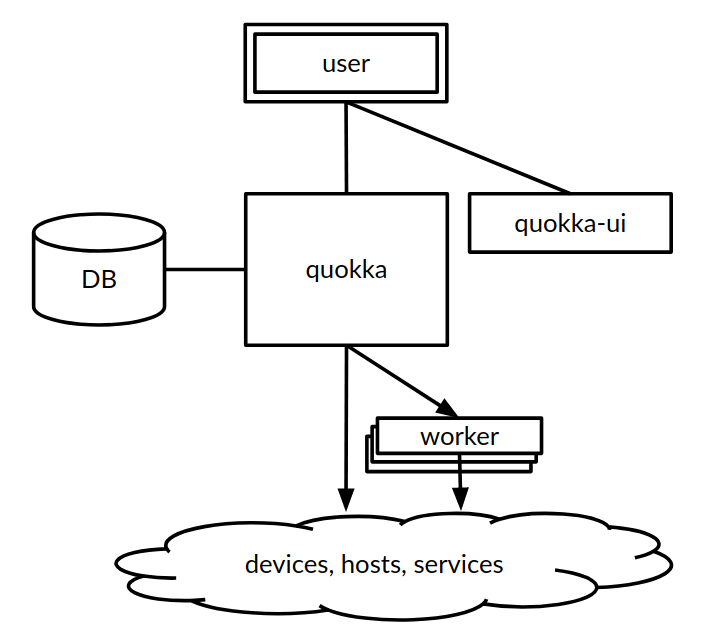
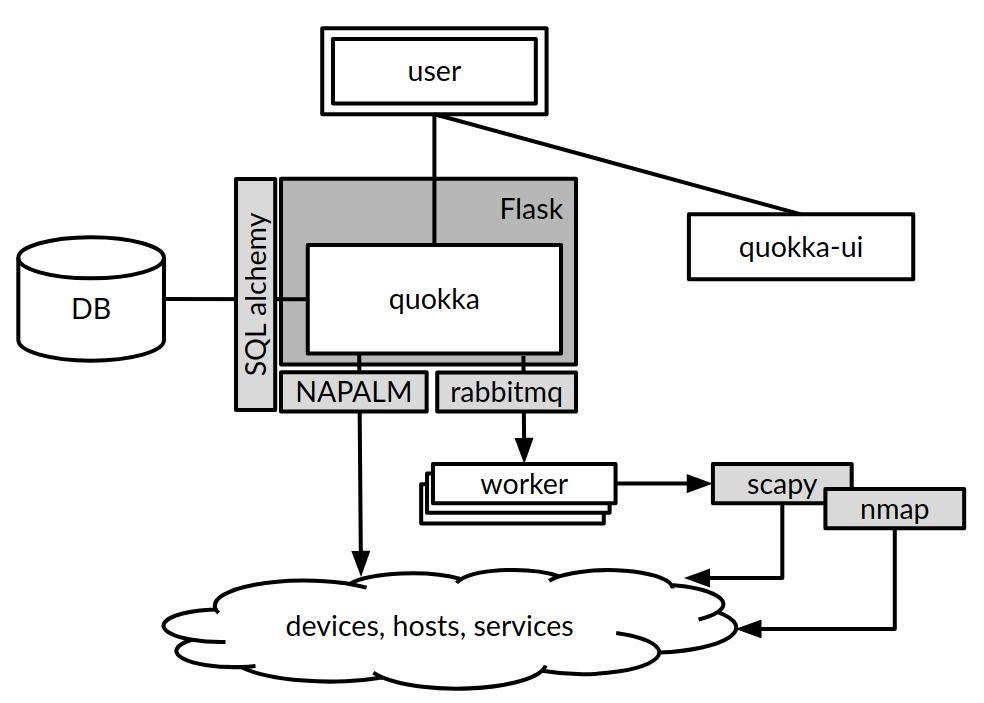
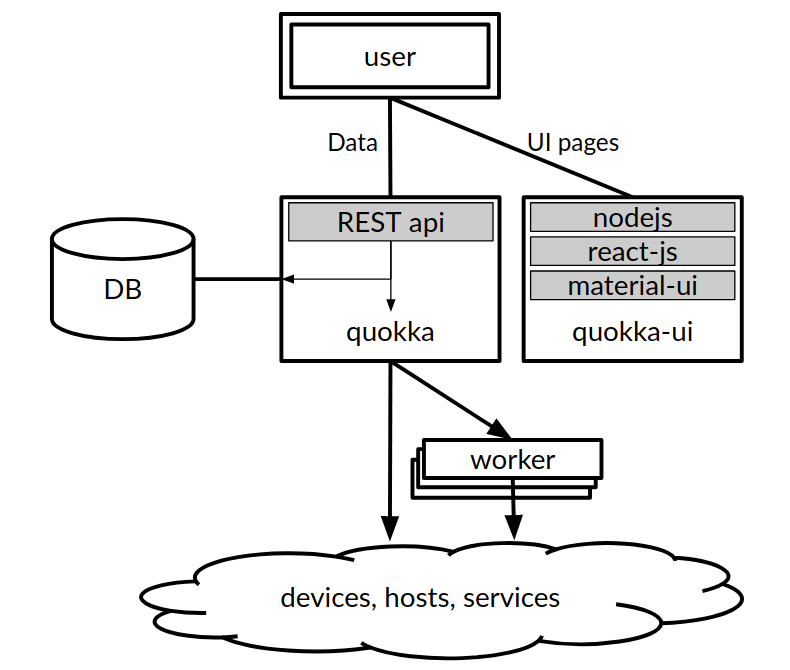
Non-functional Requirements Essential in a Network Automation Architecture
Scalability
- Scalability and low latency are achieved by combining NFV and edge computing.
- Scalability for networking computing is provided by NFV, which allows the network’s resources to be scaled up or down based on demand and application utilization (Majumdar et al., 2022).
- Low latency is provided by edge computing. Because the Edge is closer to the user, the latency time between transmitting data to thedata center and returning to the user equipment (UE) is reduced, resulting in a speedier computing experience.
Reliability
- Through NFV, network slicing is achievable. Different partitions (or slices) of the network might be designated for specific network functions.
- This approach ensures that high-bandwidth apps receive the networking capabilities they require while not interfering with the computational activities of other programs on the same network (Majumdar et al., 2022).
- This also reduces the likelihood of network issues. Edge computing increases network performance by assuring consistent services and connectivity for high-bandwidth applications and goods.
Security

- Security is a serious concern, and the numerous attack points must be considered (Majumdar et al., 2022).
- Using a vendor-certified hardware layer and enabling the following features will help to create a safe NFV environment:
- Trust in the hypervisor layer
- Access control in the MANO layer
- Network segmentation
- Traffic filtering and perimeter security in the network layer
- Continuous scanning and monitoring
- Proper Identity and Access Management (IAM) and certificate management at the VNF/application layer
References
Iyengar, A. (2021). An overview of network automation and highlights how automation is facilitated in the last mile by edge computing. IBM. https://www.ibm.org/cloud/automation-at-the-edge
Majumdar, S., Trivisonno, R., & Carle, G. (2022, May). Scalability of Distributed Intelligence Architecture for 6G Network Automation. In ICC 2022-IEEE International Conference on Communications (pp. 2321-2326). IEEE. https://doi.org/10.1109/ICC45855.2022.9838791

 Finland
Finland Germany
Germany Denmark
Denmark Sweden
Sweden Italy
Italy Netherlands
Netherlands Norway
Norway 




























No Comments